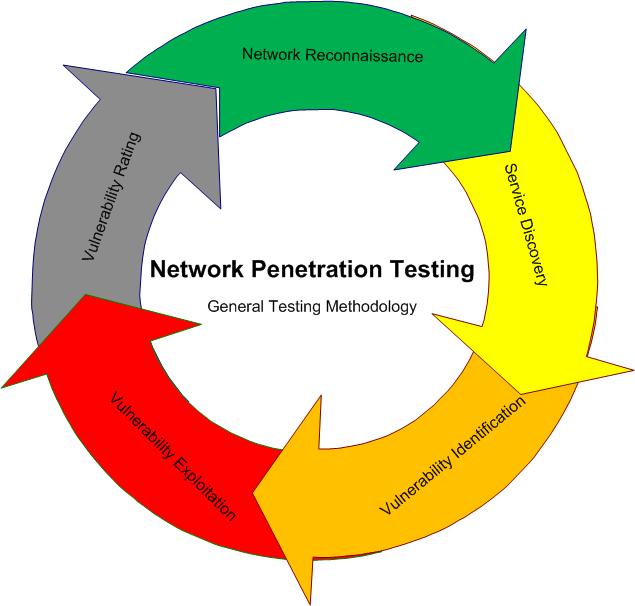
Our network security testing finds the holes in your internal and external networks that can be compromised by attack agents. We detail all vulnerabilities we identify, rank the risks they present to our client’s business, and provide a clear mitigation strategy.
Malicious attackers may find holes in your network to breach the perimeter. Once inside, they may penetrate your internal networks to do further damage. We find the vulnerabilities in your network security so you’ll know where to focus your efforts to reduce the likelihood of a breach, and you’ll have the information you need to keep your internal and customer data secure.
Security testing is a process intended to reveal flaws in the security mechanisms of an information system that protect data and maintain functionality as intended. Due to the logical limitations of security testing, passing security testing is not an indication that no flaws exist or that the system adequately satisfies the security requirements.
Typical security requirements may include specific elements of confidentiality, integrity, authentication, availability, authorization and non-repudiation. Actual security requirements tested depend on the security requirements implemented by the system. Security testing as a term has a number of different meanings and can be completed in a number of different ways. As such a Security Taxonomy helps us to understand these different approaches and meanings by providing a base level to work from.